Hijacking the flow
Exploring Dynamic Library Injection
About me
Veteran reverse-engineer
(2017-2021) - Developed Snapchat's Realtime Application Self-Protection (RASP)

Why this talk?
Many tools use Dynamic Library Injection
Users are often not aware
Why this talk?
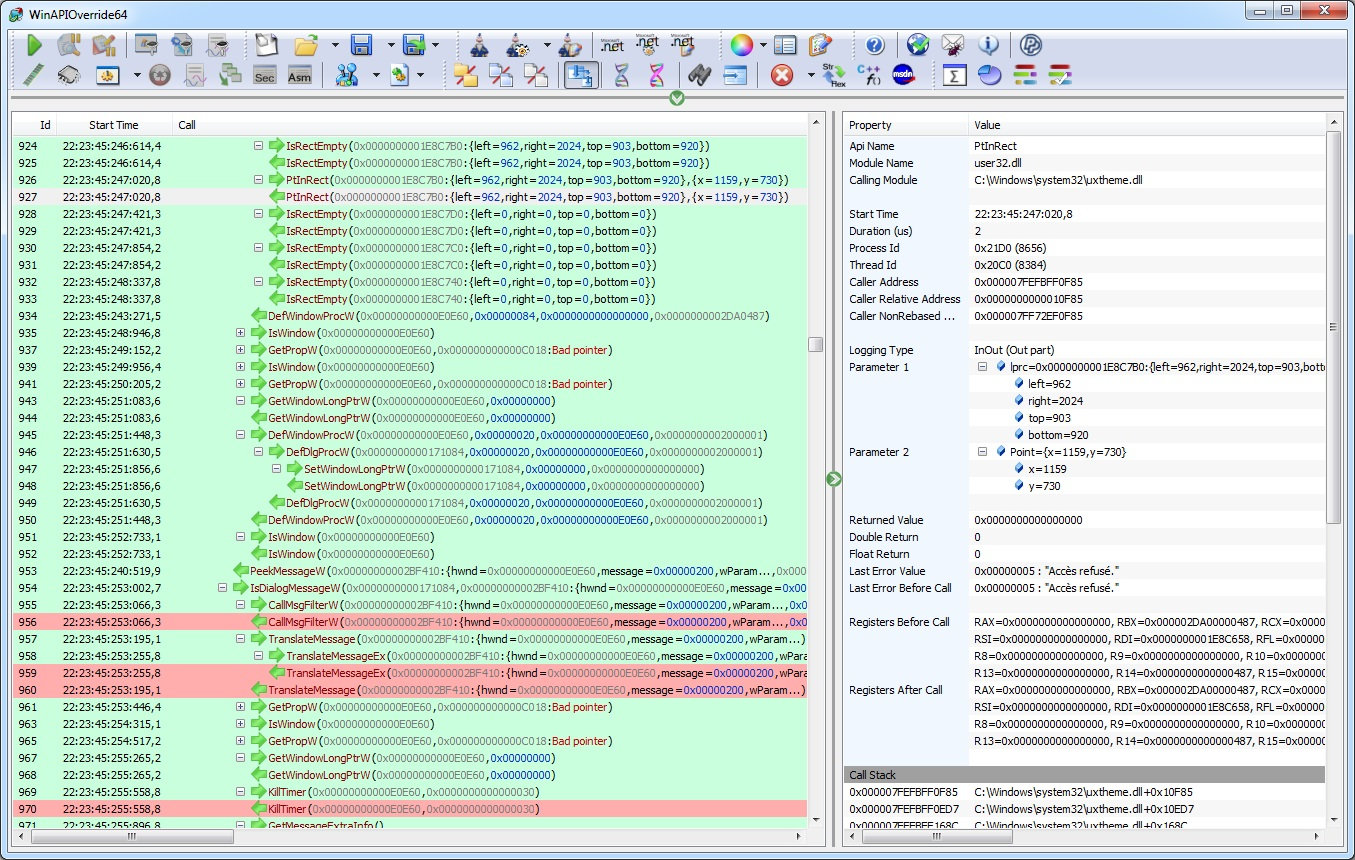

When is dynamic library injection used?
Legitimate uses
- Dynamic binary instrumentation (CydiaSubstrate, Frida, QBDI, fishook…)
- Game and app mods (Frida, CydiaSubstrate tweaks, MSN Messenger+, MelonLoader, Reshade…)
- Code coverage, perf analysis, leak detection (Frida, DynamoRIO, Intel PIN, Valgrind…)
- API Monitoring (Frida, Api monitor, WinAPIOverride…)
- Code tracing (Frida stalker, Intel PIN, Tenet…)
- Threat detection and prevention (various EDRs, antiviruses…)
- Compatibility and bug fixes (Microsoft Application Compatibility Toolkit)
- Accessibility features (NVDA and JAWS screen readers…)
When is dynamic library injection used?
Less legitimate uses
- Game cheats
- DRM bypass / game cracks
- Ad Injection
- Post-exploitation (Meterpreter, Cobalt Strike, Brute Ratel C4…)
- Code execution
- Privilege escalation
- Stealth / concealment / evasion
- Keylogging
- Data exfiltration
- Data theft (e.g. from password managers)
What is a dynamic library?
A compiled collection of code and data that can be loaded into a program's memory and executed at runtime, rather than being compiled directly into the program's executable.
What is a dynamic library?
They are typically loaded when a program starts or on-demand during execution
They have different names on different platforms
- Windows: Dynamic Link Library (.dll)
- MacOs: Dynamic Library (.dylib)
- Linux: Shared Object (.so)
What are dynamic library useful for?
Reduce app download size (when installed once for the whole system)
Reduce memory footprint (when loaded on-demand)
Centralized updates and vulnerability patching
How do dynamic libraries work ?
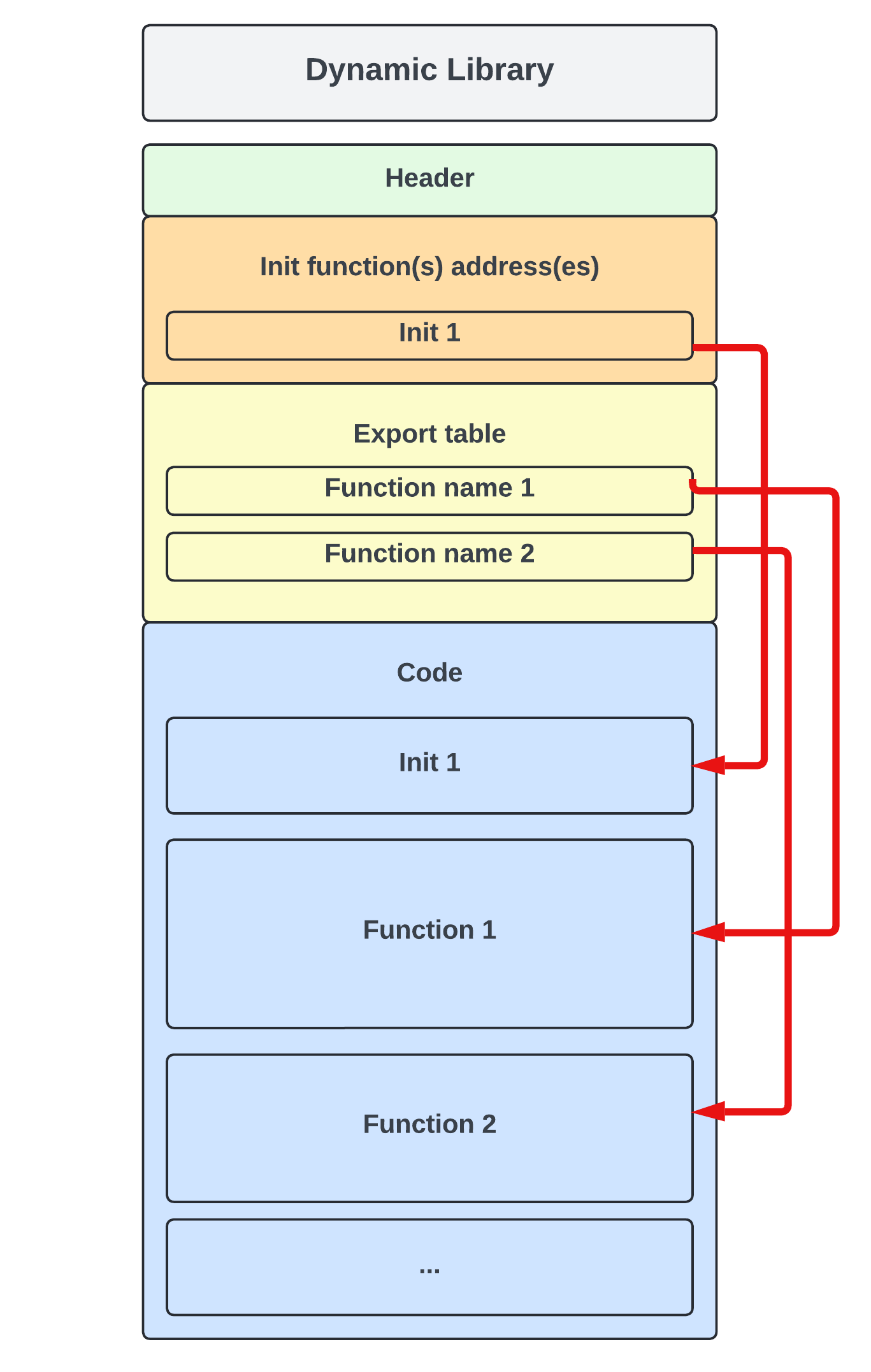
How do dynamic libraries work ?
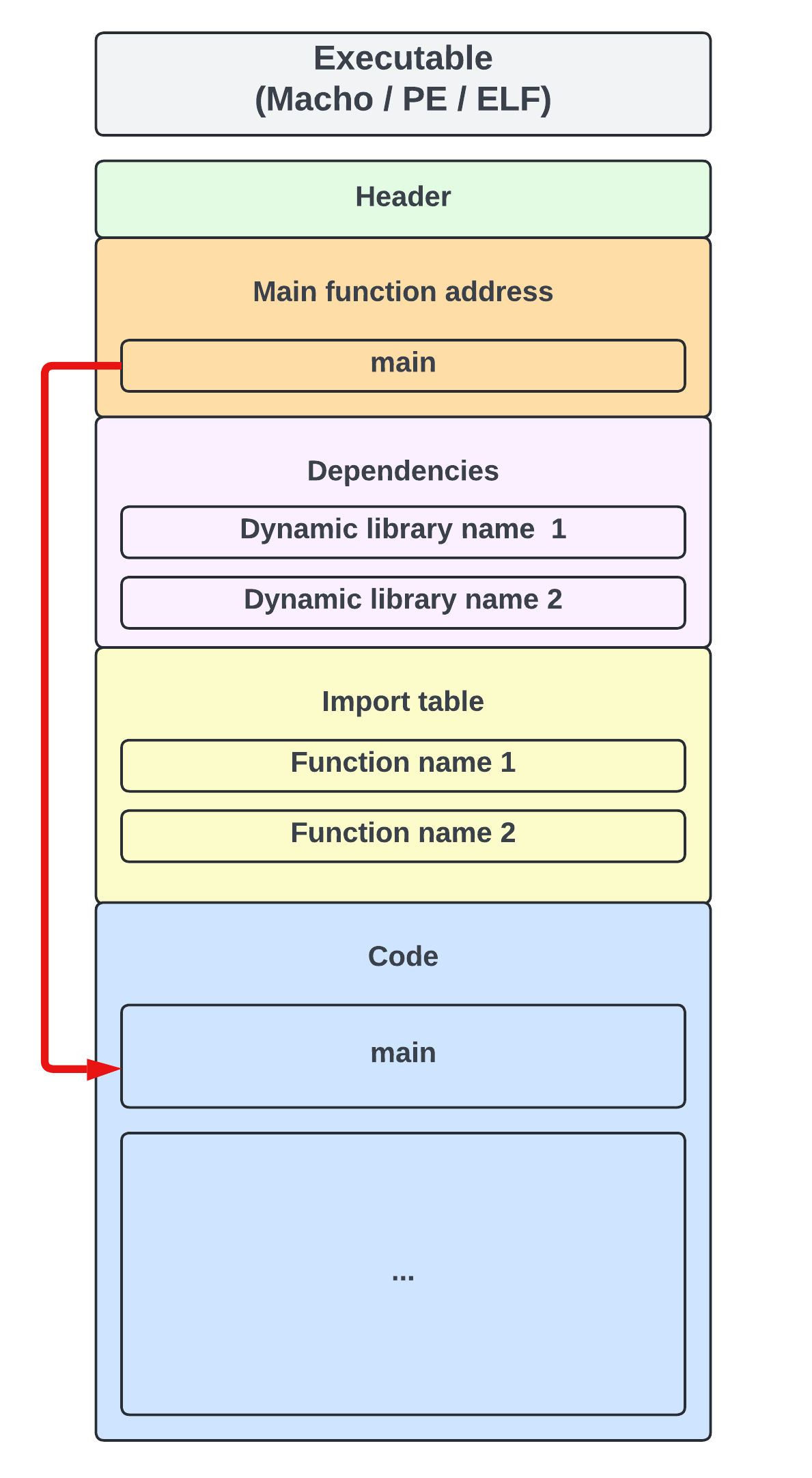
How do dynamic libraries work ?
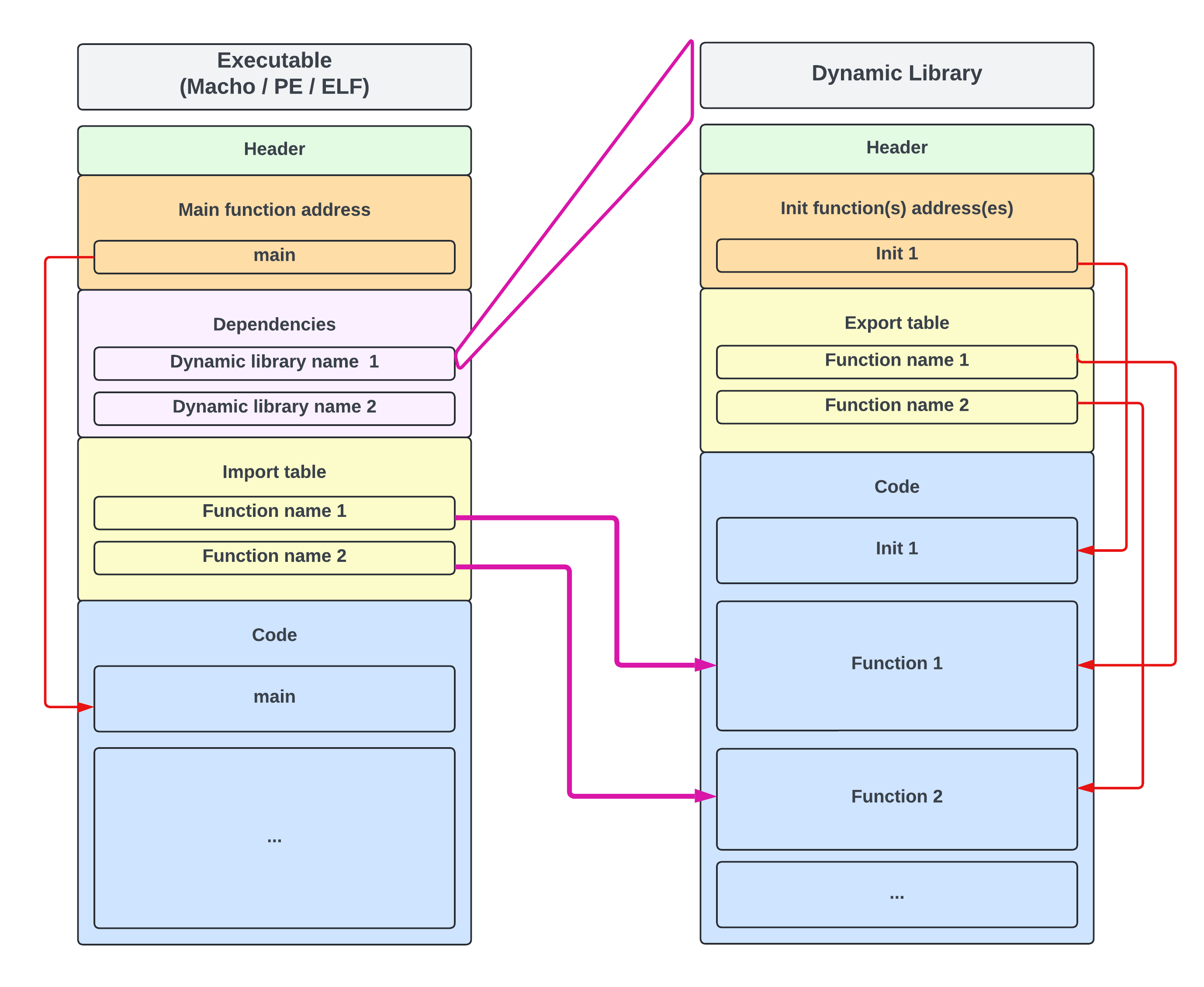
Flow hijacking (hooking)
Flow hijacking denotes several techniques used to intercept, modify, or redirect the normal execution path of a program.
Hooking means diverting a program's flow to custom code before, instead of, or after executing the original functionality.
Hooking techniques
Proxying / interposing / sideloading
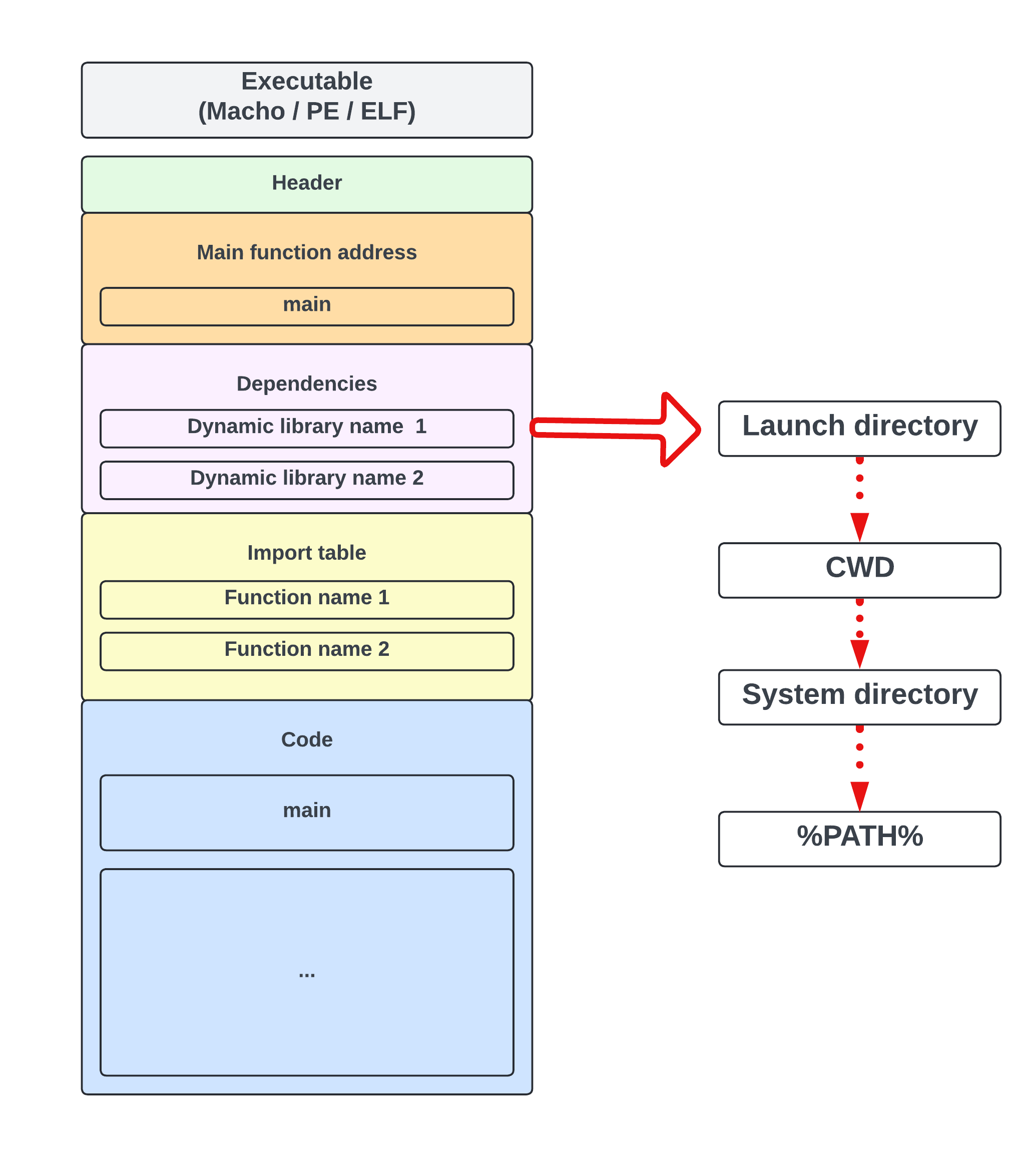
Hooking techniques
Proxying / interposing / sideloading
Hooking techniques
Proxying / interposing / sideloading
Typically abuses library search order
Can lead to RCE or privilege escalation
Only works for inter-library hooking
Hooking techniques
IAT / PLT / GOT hooking (FishHook,Api Monitor)
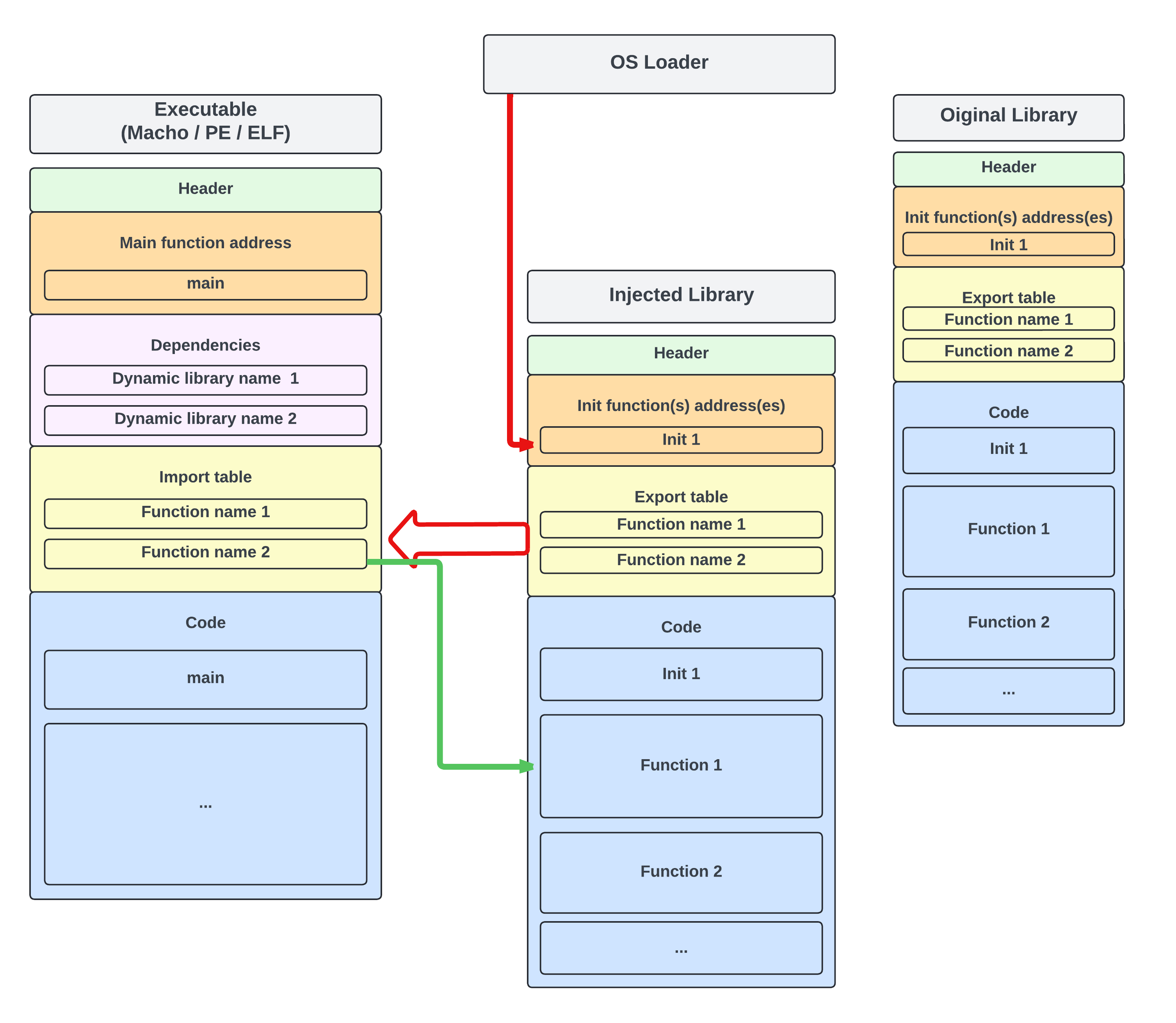
Hooking techniques
IAT / PLT / GOT hooking (FishHook,Api Monitor)
Technically easy to implement
Only works for inter-library hooking
Hooking techniques
Inline, Trampoline, Detour hooking (Frida, CydiaSubstrate, Detour)
Hooking techniques
Inline, Trampoline, Detour hooking (Frida, CydiaSubstrate, Detour)
Hooking techniques
Inline, Trampoline, Detour hooking (Frida, CydiaSubstrate, Detour)
Works on almost any function
Can be quite complicated and error prone
Requires an assembler and disassembler
When to perform the injection?
Inject during application startup
Trace the whole program startup
A target dependency can be highjacked during startup
Disable EDR / RASP / anti-cheat / code integrity before it has a chance to run
Inject in an already running application
The target is already running
A target dependency can be highjacked during on-demand loading
The EDR / RASP only performs integrity checks at startup
When to perform the injection?
Inject during application startup
Linux: LD_PRELOAD
Mac: DYLD_LOAD_LIBRARY
Windows: Various registry keys (eg. AppInitDLLs)
When to perform the injection?
Inject in an already running application
Prevention, detection and mitigation
The user is the victim
Data theft
Keylogging
Privilege escalation
The user is the attacker
Game cheating
Cracks and DRM breaks
Reverse engineering
Prevention, detection and mitigation
System wide protection
- EDRs
- Kernel anti-cheats
- EBPF modules
- Windows: Virtualisation Based Security
- Windows: Code Integrity Guard
- Windows Defender Application Control policies
- Windows: DLL Safe Search Mode (system wide)
- Linux: SELinux DENY_PTRACE
- Linux: kernel.yama.ptrace_scope
- Linux: capabilitiy CAP_SYS_PTRACE
- Mac: System Integrity Protection
Prevention, detection and mitigation
Per application protection
- Code and data integrity (at regular intervals)
- List loaded modules and check for unexpected ones
- Check the address of sensitive functions reside in the expected modules
- Check if env. variables like LD_PRELOAD are set
- Check if a debugger or ptrace are attched to the process
- Self-hooking (loadLibrary or dlopen)
- Self-debugging
Prevention, detection and mitigation
Per application protection
- Mac: PTRACE_DENY_ATTACH
- Mac: "__RESTRICT,__restrict" code section
- Mac: App sandbox
- Mac: Hardened runtime
- Windows: Safe DLL search order (per app)
- Windows: Protected Process Light
- Windows: Silos
- Windows: Application Manifest
- Linux: prctl/PR_SET_DUMPABLE